Welcome to Trezor.io/Start
Trezor.io/Start is the official onboarding page for setting up your Trezor hardware wallet safely and correctly. Whether you are using a Trezor Model T or Trezor One, this guide walks you through the entire setup process—from connecting your device, installing firmware, creating a secure recovery seed, setting a PIN, and using Trezor Suite to manage your crypto assets. The purpose of this page is to ensure that every user completes the setup using safe, verified steps so that funds remain fully protected at all times.
Trezor is a hardware wallet designed to protect private keys from exposure to internet-connected devices. By storing your private keys offline, Trezor minimizes risks such as malware, phishing attacks, or unauthorized access. Trezor.io/Start provides official instructions so that beginners as well as experienced crypto users can configure their device without confusion. Each step focuses on long-term security and helps ensure your crypto remains safe, recoverable, and accessible only by you.
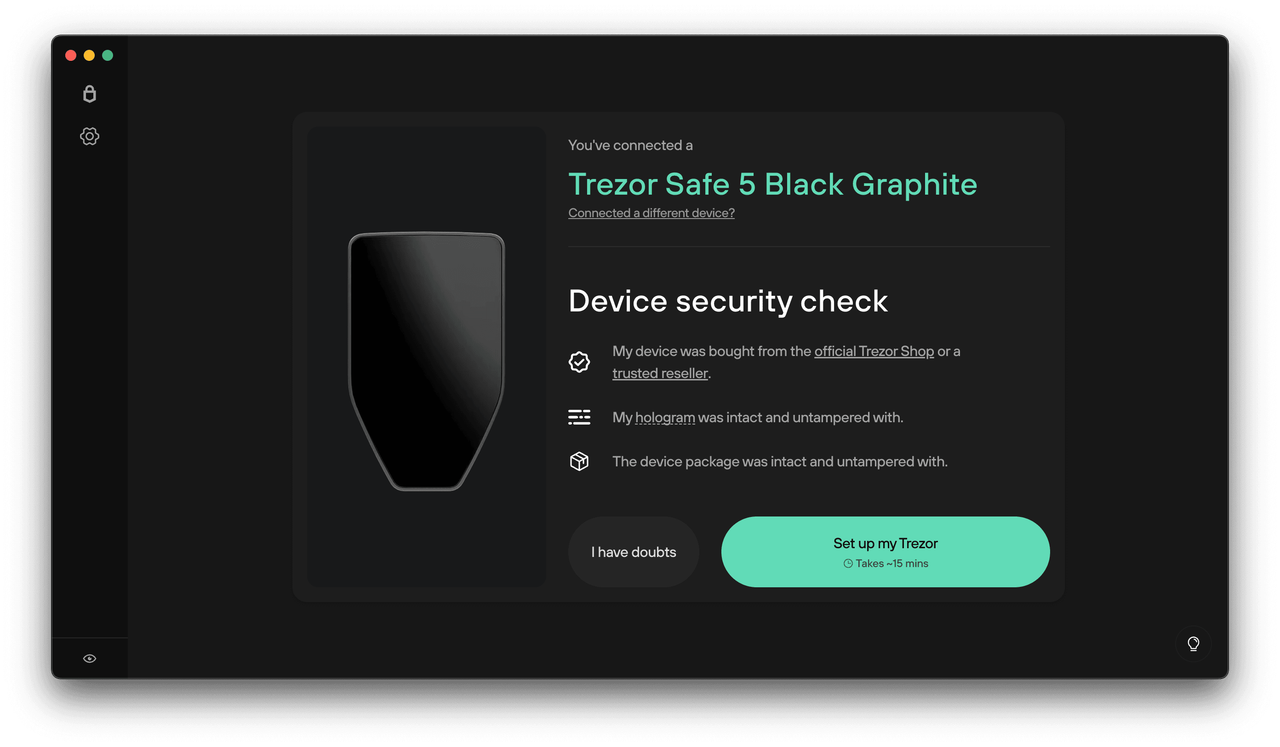
Step 1: Connect Your Trezor Device
Begin by connecting your Trezor hardware wallet to your computer using the official USB cable that came with your device. Once connected, your browser or Trezor Suite will automatically detect the device. It is important to verify the hologram seal on new Trezor units to confirm tamper-free packaging. Only use the official Trezor.io/Start page to avoid fraudulent clones or phishing websites pretending to be Trezor support.
Step 2: Install Trezor Suite
Trezor Suite is the official desktop application that allows you to manage your cryptocurrency portfolio securely. Download Suite directly from the official website to ensure authenticity. Suite includes tools for portfolio tracking, sending and receiving crypto, verifying addresses, customizing device settings, and enabling advanced security options. Keeping Suite updated is essential because updates include security improvements, new features, and expanded asset support.
Step 3: Install or Update Firmware
When you connect your Trezor for the first time, it may not have firmware installed. Trezor.io/Start will prompt you to install the latest firmware version. Firmware ensures your device runs safely and supports the newest security features. Always double-check that your computer screen matches the prompts on your Trezor device. The device requires physical confirmation for firmware installation, ensuring complete user control.
Step 4: Create Your Recovery Seed
Your recovery seed, also known as a backup seed phrase, is the most important part of securing your wallet. It consists of 12, 18, or 24 words displayed on your device. These words are generated offline inside the hardware wallet. Write them down carefully on paper and keep them stored securely in a private location. Never take a photo, upload it to the cloud, or type it into any digital device. Anyone with your seed can access your funds, so treat it as your master key.
Step 5: Set a Strong PIN
Your PIN protects your Trezor wallet from unauthorized physical access. Each time you connect the device, you must enter the PIN to unlock it. Trezor displays randomized keypad positions on your device screen, ensuring that even if your computer is compromised, the PIN entry remains safe.
Step 6: Use Trezor Suite to Manage Crypto
Once setup is complete, you can begin managing your crypto assets through Trezor Suite. You can send, receive, store, and track assets like Bitcoin, Ethereum, and many supported coins. All transactions require confirmation on your device, meaning no transaction can occur without your approval.
Important Security Tips
• Never share your recovery seed with anyone. • Always verify you are on the official Trezor.io website. • Keep Trezor Suite updated. • Store your device and recovery seed in separate, safe locations. • Only purchase Trezor devices from authorized sellers.
Your Crypto Security Starts Here
By following the instructions at Trezor.io/Start, you ensure your crypto assets remain protected from digital threats and unauthorized access. Completing these steps establishes a solid foundation for long-term crypto security and peace of mind.